https://www.csoonline.com/article/3148823/10-essential-powershell-security-scripts-for-windows-administrators.html
10 essential PowerShell security scripts for Windows administrators
PowerShell is a valuable tool for automating Windows administration tasks, including laborious security chores

In the 12 years since Microsoft released PowerShell, it has become the de facto tool to dependably administer servers. In August of 2016, it was made open-source and cross-platform with the introduction of PowerShell Core. Microsoft also purchased Github in June 2018, making it the home of the increasing catalog of PowerShell scripts.
CSO has identified ten of those scripts that should be part of your security team’s toolbox. You can use some of the scripts below to add security. Some let you review the security status of a network. Others allow you to see what an attacker would do to a system. All show that PowerShell is now a key part of a Windows administrator’s toolkit.
These 10 PowerShell scripts should not be considered standalone, but as a much larger collection of tools needed to manage workstations and servers. Even attackers acknowledge that PowerShell is key to controlling workstations making PowerShell a key way that attackers pivot and do lateral movement on a network once they gain access.
As always, remember that if you have not run PowerShell scripts on a system, you have to adjust the settings to allow them to run. If Execution-Policy is not already set to allow running scripts, then manually set it as below and then use the readiness script: Set-ExecutionPolicy Unrestricted, and then adjust the Execution policy to the setting desired in your firm.
1. POSH-Sysmon: Configuring Sysmon
Microsoft’s Sysmon is a tool that monitors systems and adds granular events to be tracked even after a reboot. For any edge based system or public-facing web server, I strongly recommend installing and configuring Sysmon to better track future attacks. You should anticipate that you will be attacked and thus plan accordingly.
However, configuring each system independently can be a hassle. Thus, the PowerShell script POSH-Sysmon is based on PowerShell 3.0 or above and adds the ability to use PowerShell to easily create and manage Sysinternals Sysmon v2.0 config files. Sysmon collects the events it generates using Windows Event Collection or SIEM agents. You can then analyze them and then identify malicious or anomalous activity and understand how intruders and malware operate on the network. As noted in the blog, a sample event that can be tracked using the ProcessAccess filter for Local Security Authority Subsystem Service (LSASS) to detect if a malicious process is trying to extract credentials from memory.
2. Enable the Client Rules Forwarding Block control: Email hardening
One way that attackers can exploit Office 365 is to obtain access to the credentials of an Office 365 user and then set up a silent rule in Outlook to forward financial or attack emails to the attacker. Thus, you should determine if you can block all forwarding rules proactively.
You can easily enable the PowerShell command Enable Client Rules Forwarding Blocks by going to the Microsoft 365 Secure Score. However, you can use individual PowerShell commands to review if there is a forwarding set up and disable it accordingly. The command Set-RemoteDomain [remote domain name] -AutoForwardEnabled $false ensures that attackers can send emails from your network without you knowing about it. Take the time to review email forwarding rules to ensure your domain hasn’t already been attacked by phishing or abused in attacks.
3. Remove-LocalAdmins Masiv: Local administrator review
One key way to reduce lateral attacks in a network is to remove common local administrator passwords. A longstanding script you can use is the Remove-LocalAdmins Masive script, which is still a key tool to look at all the computers specified in a text file for all the users listed in another file, and then remove those users.
The Local Administrator Password (LAPS) toolkit allows you to set random local administrator passwords in a domain to ensure that pass-the-hash attacks do not occur. Then you can use the LAPS Reporting PowerShell script to audit the use of the LAPS toolkit or use a LAPSpass to retrieve a password for a single user.
4. MicroBurst: Azure PowerShell scripts
The new kid on the block is the cloud, and PowerShell brings new meaning to both secure and understand how attackers use PowerShell in attacks. MicroBurst is a collection of PowerShell scripts that support Azure Services discovery, weak configuration auditing, and post exploitation actions such as credential dumping. It is intended to be used during penetration tests where Azure is in use. In a YouTube video from an October 2008 session at Derbycon, Karl Fosaaen presents techniques on how attackers can go after Azure resources. By understanding how attackers go after Azure resources, you can better protect your setup.
5. SecurityPolicyDsc: Local security policies
Anytime you can be consistent in how you set up computers makes it easier to control and maintain them. PowerShell can be used to set local security policies with the PowerShell script SecurityPolicyDsc. You can then follow the guidance located at the Center for Internet Security or provided by NIST.gov to set a hardened operating system. It’s key that you test how enabling or disabling settings impacts your environment. Once you have set a standard workstation, you can then use PowerShell to recreate the settings across your organization including standalone workstations or kiosk machines.
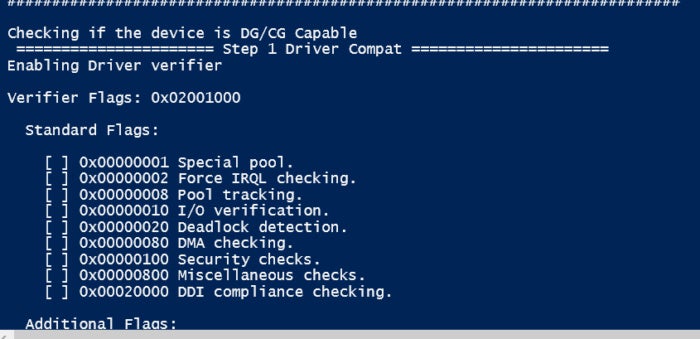
6. Device Guard and Credential Guard: Deploying secure systems
When configuring Windows 10 on workstations, it’s critical to ensure that Exploit Guard, Application Guard and Credential Guard are enabled and deployed. You can use PowerShell to determine if machines are able to support these enhanced technologies as well as deploy settings using ConfigMgr.
Microsoft provides the Device Guard and Credential Guard hardware readiness tool, which is a Windows PowerShell script. Run it with elevated permissions on Windows 10 (beginning with version 1607) and Windows Server 2016 and now Server 2019. The tool can check if the device can run Device Guard or Credential Guard, check for compatibility with the Hardware Lab Kit tests that are run by partners, enable and disable Device Guard or Credential Guard.
You can also use it to check the status of Device Guard or Credential Guard on the device. The script integrates with System Center Configuration Manager or any other deployment mechanism to configure registry settings that reflect the device capabilities.
Finally, you can use an embedded ConfigCI policy in audit mode that enables Device Guard by default when a custom policy is not provided. It has various switches that can be used to review your options including the flags of to review as well as enable the setting: DG_Readiness.ps1 -[Capable/Ready/Enable/Disable/Clear] -[DG/CG/HVCI] -[AutoReboot] –Path
7. NTFSSecurity: File system security
This script allows for a much easier management of permissions on files and folders. This NTFSSecurity allows for additional granular controls for managing permissions with PowerShell. Doing so in Native PowerShell is only a bit easier than in VBS [VBScript?] or the command line as it has no cmdlets for most day-to-day tasks such as getting a permission report or adding permission to an item. PowerShell only offers Get-Acl and Set-Acl. NTFSSecurity enhances the options available, allowing you to get, add or remove various permissions.
8. Posh-SecMod: Network discovery
The ability to review what others can see on your network can reveal how it might be exploited. This technique is called network discovery. Posh-SecMod is a bundle of scripts, several of which assist with network discovery. Included in the collection are the following functions:
- Discovery: Perform network discovery.
- Parse: Parsers for Nmap, DNSRecon and other types of output files from security tools.
- PostExploitation: Functions to help in performing post exploitation tasks.
- Registry: Collection of functions for manipulating the registry in remote hosts using WMI.
- Utilities: General purpose functions.
- Audit: Functions that may be useful when performing an audit of systems.
- Database: Functions that are useful when interacting with databases.
Also included are modules that allow easier control of Nessus, Shodan, VirusTotal and Metasploit modules.
9. MonitorADGroupMembership: Monitoring movement
Often in Active Directory attacks, the attacker gains access through a phishing attack. Once an exploit is in place, they can change group membership to the administrator group. One script that can monitor this change is MonitorADGroupMembership. You can also set it up to send an email when someone is changing the membership.
10. BlackViperScript: Standalone workstation hardening
The BlackViper website has recommended various workstation hardening techniques for many years. Now the settings are included in BlackViperScript. This script lets you set Windows 10's services based on Black Viper's service configurations, your own service configuration (if in a proper format), a backup of your service configurations made by this script, or a custom configuration using the script.
PowerShell is a powerful tool that can be used in multiple ways. These ten scripts or topics just scratch the surface of what can be done with PowerShell. You can keep track of what PowerShell repositories are trending by keeping an eye on Github.
This story, "10 essential PowerShell security scripts for Windows administrators" was originally published by InfoWorld.