Mikrotik - parte 1 - usado para minerar
Massive Coinhive Cryptojacking Campaign Touches Over 200,000 MikroTik Routers

The campaign appears to have gotten off the ground this week and was, in its first stages, mainly active in Brazil, but later started targeting MikroTik routers all over the world.
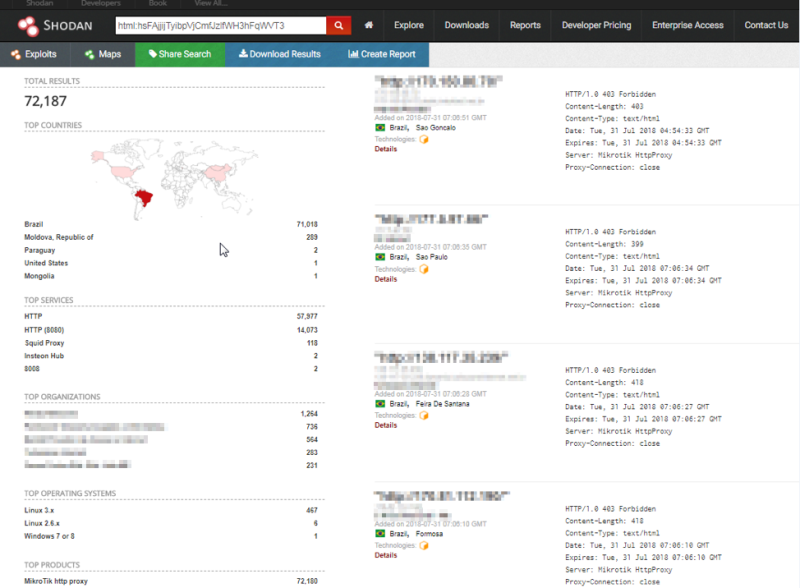
In a report Trustwave shared with Bleeping Computer, Kenin says that the hacker (or hackers) behind this campaign appear to have compromised around 72,000 MikroTik routers in Brazil during the first stages of their attack.another mass exploitation against @mikrotik_com devices (https://t.co/4MxQbnNStA)— MalwareHunterBR (@MalwareHunterBR) July 30, 2018
hxxp://170.79.26.28/
CoinHive.Anonymous('hsFAjjijTyibpVjCmfJzlfWH3hFqWVT3', #coinhive pic.twitter.com/Nr8MA0TbzY
Hacker using April 2018 MikroTik zero-day
According to Kenin, the attacker used one of those PoCs to alter traffic passing through the MikroTik router and inject a copy of the Coinhive library inside all the pages served through the router.We know it's only one threat actor exploiting this flaw because the attacker used only one Coinhive key for all the Coinhive injections he performed during the past week.
Furthermore, Kenin says that he also identified some cases where non-MikroTik users were also impacted. He says this was happening because some Brazilian ISPs were using MikroTik routers for their main network, and hence the attacker managed to inject the malicious Coinhive code in a massive amount of web traffic.
In addition, Kenin says that because of the way the attack was performed, the injection worked both ways, and not necessarily only for traffic going to the user. For example, if a website was hosted on a local network behind an affected MikroTik router, traffic to that website would also be injected with the Coinhive library.
Hacker became more careful, shrunk operation
But injecting Coinhive in so much traffic is very noisy and tends to annoy users, which could lead to users and ISPs investigating the source of the problem, such as it happened with this user on Reddit.The attacker also appears to have understood this issue, and Kenin says that in recent attacks, the hacker switched tactics and only injected the Coinhive script in error pages returned by the routers.
But shrinking his attack surface doesn't look to be a downgrade for the attacker. The Trustwave researcher says that in recent days he's seen the attack spreading outside Brazil, and has now more than doubled the initial numbers, having altered configurations and added the Coinhive injection on over 170,000 MikroTik routers.
"Let me emphasize how bad this attack is," Kenin says. "There are hundreds of thousands of these devices around the globe, in use by ISPs and different organizations and businesses, each device serves at least tens if not hundreds of users daily."
"The attacker wisely thought that instead of infecting small sites with few visitors, or finding sophisticated ways to run malware on end user computers, they would go straight to the source; carrier-grade router devices," he added.
"Even if this attack only works on pages that return errors, we're still talking about potentially millions of daily pages for the attacker."
The attack has room to grow
A query on the Shodan IoT search engine reveals that there are over 1.7 million MikroTik routers available online.Bleeping Computer has reached out to the Coinhive team and inquired if they've taken down this site key, and how much Monero the attacker mined through his scheme.
UPDATE: Shortly after this article's publication, security researcher Troy Mursch told Bleeping Computer he discovered a second Coinhive key being injected in the traffic of MikroTik routers. This campaign has touched over 25,000 routers, bringing the total at over 200,000, as the first Coinhive key was now used on over 175,000 devices. It is unclear if this second campaign is being orchestrated by another hacker, or by the same threat actor who switched to a new key after Trustwave exposed his first operation. Article title was also updated.
Coinhive site key "oDcuakJy9iKIQhnaZRpy9tEsYiF2PUx4" is used in another #cryptojacking campaign targeting MikroTik routers. In this case, over 25,000 affected hosts are found on @censysio— Bad Packets Report (@bad_packets) August 2, 2018
h/t @onyphehttps://t.co/M9iLatsIVX